
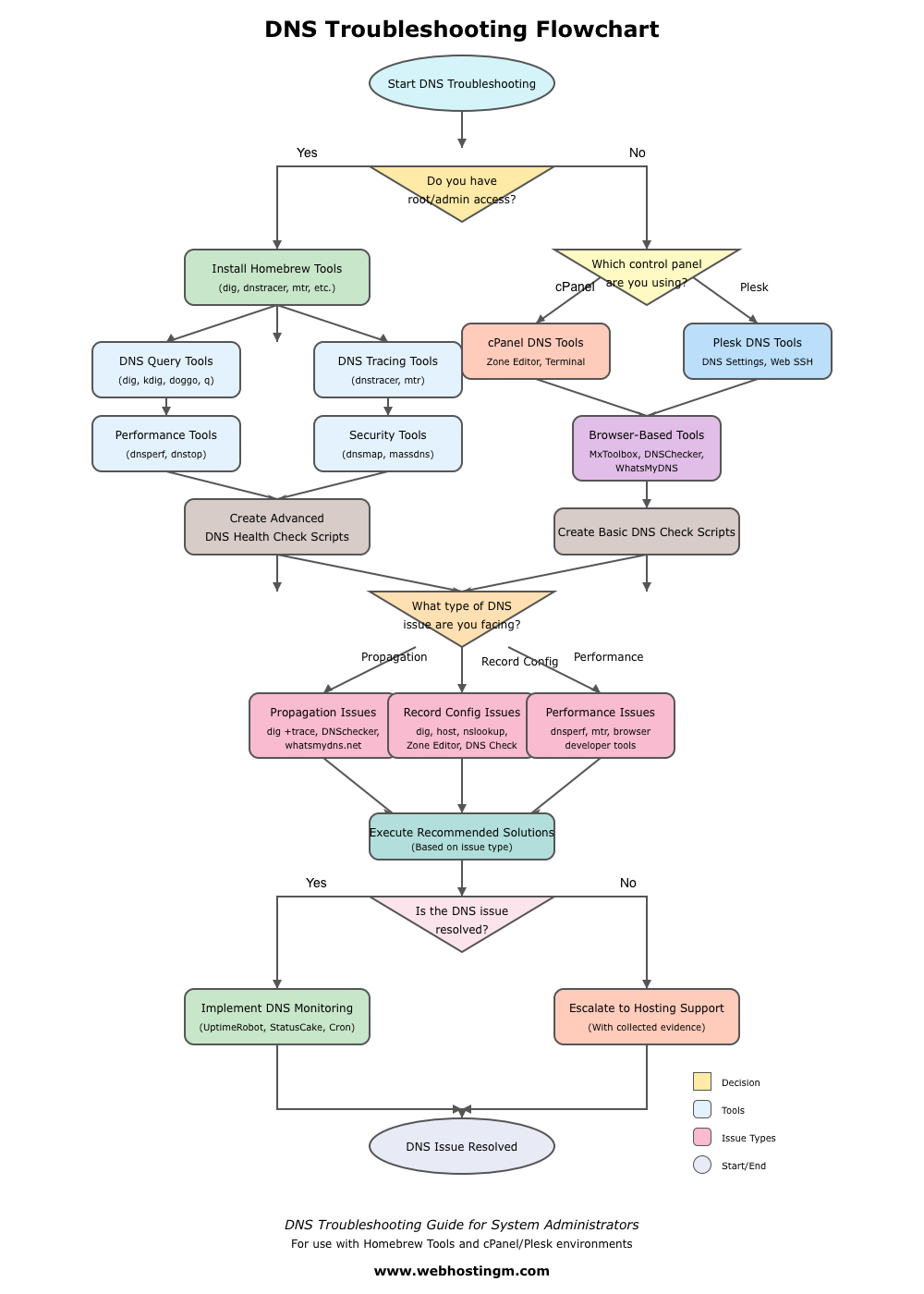
DNS troubleshooting is a critical skill for system administrators managing web servers and network infrastructure. This guide covers essential tools that help inspect, debug, and verify DNS queries across Linux, macOS, and Unix-based systems.
What is DNS Query Inspection?
DNS query inspection is the systematic analysis and monitoring of DNS traffic to identify performance issues, security threats, and configuration errors. It involves examining query patterns, resolution times, error rates, and response data to ensure optimal DNS health.
Suppose you are sysadmin or dealing with I.T infrastructure of any kind. In that case, you already know that an effective DNS query inspection is crucial for maintaining robust, secure, and high-performing DNS infrastructure. By systematically examining DNS configurations, query patterns, and resolution processes across all environments (from shared hosting to enterprise infrastructure), you can identify and resolve issues before they impact your services. Proper DNS inspection also helps maintain website availability, defend against DNS-based attacks, and troubleshoot network issues before they impact users.
Table of Contents
- Prerequisites
- Shared Hosting Environments (cPanel & Plesk)
- Linux VPS and Dedicated Servers
- Cloud Platform DNS Services
- Enterprise-Level DNS Infrastructure
- DNS Security Best Practices
- Systematic Troubleshooting
- Modern DNS Inspection Tools
Prerequisites
Before beginning DNS query inspection, ensure you have the following:
- Administrative access to your DNS management interface
- DNS utilities installed on your system
- Basic understanding of DNS record types and resolution process
- Network access to query relevant nameservers
$ sudo apt-get update
$ sudo apt-get install dnsutils bind9utils whois net-tools tcpdump
This installs essential DNS troubleshooting tools including dig, nslookup, host, whois, and packet capture utilities.
Shared Hosting Environments (cPanel & Plesk)
cPanel DNS Inspection
In cPanel environments, DNS for the whole domains hosted on the server is typically managed through WHM (Web Host Manager) for administrators, with individual domain settings accessible through the cPanel interface for end users.
Using WHM Interface
- Log into WHM as admin (typically at https://server-ip:2087)
- Navigate to "DNS Functions" > "DNS Zone Manager"
- Select the domain to inspect and review the records for correctness
Command Line Inspection on cPanel Servers
$ cat /var/named/domain.com.db
This command displays the raw zone file for the specified domain, allowing you to verify all DNS records directly.
Enabling Query Logging
# Edit named configuration
$ vi /etc/named.conf
# Add the following logging configuration
logging {
channel query_logging {
file "/var/log/named/queries.log" versions 3 size 5m;
severity dynamic;
print-time yes;
};
category queries { query_logging; };
};
# Create log directory if it doesn't exist
$ mkdir -p /var/log/named
$ chown named:named /var/log/named
# Restart named service
$ systemctl restart named
This configuration enables detailed query logging, which is essential for identifying unusual query patterns or potential DNS-based attacks.
$ tail -f /var/log/named/queries.log
$ grep -i "client" /var/log/named/queries.log | awk '{print $3}' | sort | uniq -c | sort -nr
The first command shows real-time DNS queries, while the second analyzes log data to identify the most active clients, which can help detect abnormal query patterns.
Plesk DNS Inspection
Using Plesk Interface
- Log into Plesk admin panel
- Navigate to "Domains" > select domain > "DNS Settings"
- Review DNS records for accuracy and completeness
Command Line Inspection on Plesk Servers
$ plesk bin dns --info domain.com
$ cat /var/named/run-root/var/domain.com.hosts
$ dig @localhost domain.com any
These commands help verify DNS configuration in Plesk environments, showing the zone information and testing local resolution.
Enable Bind Query Logging in Plesk
# Edit Bind configuration
$ vi /etc/bind/named.conf
# Add logging section
logging {
channel query_log {
file "/var/log/bind/query.log" versions 3 size 10m;
print-time yes;
severity info;
};
category queries { query_log; };
};
# Create log directory
$ mkdir -p /var/log/bind
$ chown bind:bind /var/log/bind
# Restart Bind service
$ systemctl restart bind9
This configures BIND (the DNS server used by Plesk) to log all incoming queries, which is valuable for debugging and security monitoring.
Linux VPS and Dedicated Servers
With full server access, you can implement more sophisticated DNS query inspection methods.
BIND DNS Server Inspection
$ named-checkconf /etc/named.conf
$ named-checkzone domain.com /var/named/domain.com.zone
These commands validate your BIND configuration and zone files, identifying syntax errors before they cause service disruptions.
Enable BIND Statistics for Apache 2.4+
# Configure named.conf
options {
...
statistics-file "/var/named/data/named_stats.txt";
};
# Generate statistics
$ rndc stats
# View statistics
$ cat /var/named/data/named_stats.txtThis enables BIND's built-in statistics collection, providing valuable data on query types, response codes, and cache efficiency.
DNS Packet Capture
$ tcpdump -nn -i any port 53 -w dns_capture.pcap
$ tcpdump -nn -r dns_capture.pcap
The first command captures all DNS traffic to a file, while the second allows you to analyze the captured packets. This is useful for deep inspection of DNS query patterns and identifying potential issues.
PowerDNS Inspection
$ pdns_control current-config
$ pdns_control show "*"
$ pdnsutil list-all-zones
$ pdnsutil list-zone domain.com
These commands retrieve PowerDNS configuration, statistics, and zone information, helping you verify the server's operation and zone data.
Testing DNSSEC in PowerDNS
$ pdnsutil check-zone domain.com
$ pdnsutil show-zone domain.com
These commands verify DNSSEC configuration and display detailed zone information, including signing status and key details.
Cloud Platform DNS Services
Google Cloud Platform (GCP)
$ gcloud dns managed-zones list
$ gcloud dns managed-zones describe my-zone-name
$ gcloud dns record-sets list --zone=my-zone-name
$ gcloud dns managed-zones describe my-zone-name --format="get(dnssecConfig)"
These commands provide comprehensive information about your GCP DNS zones, including records and DNSSEC status.
Enable GCP DNS Query Logging
$ gcloud dns managed-zones update my-zone-name --dns-logging
This enables logging of DNS queries in Cloud Logging, allowing you to monitor and analyze query patterns.
Amazon Web Services (AWS)
$ aws route53 list-hosted-zones
$ aws route53 get-hosted-zone --id /hostedzone/Z1234567890ABC
$ aws route53 list-resource-record-sets --hosted-zone-id Z1234567890ABC
These AWS CLI commands retrieve information about your Route 53 hosted zones and record sets.
Enable AWS Route 53 Query Logging
$ aws route53 create-query-logging-config \
--hosted-zone-id Z1234567890ABC \
--cloud-watch-logs-log-group-arn arn:aws:logs:us-east-1:123456789012:log-group:route53-queries
This command enables query logging for a Route 53-hosted zone, sending logs to a CloudWatch log group for analysis.
Oracle Cloud Infrastructure (OCI)
$ oci dns zone list --compartment-id ocid1.compartment.oc1..example
$ oci dns zone get --zone-name-or-id example.com
$ oci dns record get --zone-name-or-id example.com --domain example.com
These OCI CLI commands retrieve DNS zone and record information for inspection and verification.
Enterprise-Level DNS Infrastructure
DNS Hierarchy Inspection
#!/bin/bash
# Save as dns_map.sh and make executable with: chmod +x dns_map.sh
for d in $(cat domains.txt); do
echo "Domain: $d"
echo "Authoritative nameservers:"
dig +short NS $d
echo "SOA record:"
dig +short SOA $d
echo "--------------"
done
This script maps your DNS infrastructure by checking the nameservers and SOA records for multiple domains, helping you verify consistency across your DNS hierarchy.
Global DNS Testing
$ for ns in $(dig +short NS example.com); do echo "Testing $ns:"; mtr -r $ns; doneThis command tests network connectivity to each authoritative nameserver, helping identify potential network issues affecting DNS resolution.
Enterprise Monitoring Setup
# /etc/prometheus/prometheus.yml
scrape_configs:
- job_name: 'bind_exporter'
static_configs:
- targets: ['dns1:9119', 'dns2:9119']
# Sample alerting rule
groups:
- name: dns_alerts
rules:
- alert: HighDNSQueryRate
expr: rate(bind_incoming_queries_total[5m]) > 1000
for: 10m
labels:
severity: warning
annotations:
summary: "High DNS query rate"
description: "DNS server {{ $labels.instance }} is experiencing high query rate"
This configuration sets up Prometheus to monitor DNS servers and alerts on anomalous query rates, which is essential for proactive DNS management in enterprise environments.
DNS Security Best Practices
DNSSEC Implementation and Verification
$ dig +dnssec example.com
$ dig DNSKEY example.com +short
$ dig DS example.com @a.gtld-servers.net
$ delv example.com
These commands verify DNSSEC implementation, checking the chain of trust from the root down to your domain.
DNS Query Encryption Testing
$ sudo apt-get install knot-dnsutils
$ kdig +tls example.com @1.1.1.1
This tests DNS resolution over an encrypted TLS connection, which enhances privacy and security by preventing eavesdropping on DNS queries.
$ curl -H 'accept: application/dns-json' \
'https://cloudflare-dns.com/dns-query?name=example.com&type=A'
This tests DNS resolution over HTTPS, another encrypted option that can bypass network-level DNS filtering.
DNS Firewall and Rate Limiting
# Add to /etc/named.conf
options {
rate-limit {
responses-per-second 10;
window 5;
slip 0;
exempt-clients { 192.168.1.0/24; };
};
};
This configures BIND to limit the rate of responses to prevent DNS amplification attacks while exempting internal networks from the limits.
$ iptables -A INPUT -p udp --dport 53 -m hashlimit \
--hashlimit-name DNS --hashlimit-above 20/second \
--hashlimit-mode srcip --hashlimit-burst 100 \
-j DROP
This iptables rule limits incoming DNS queries at the network level, providing an additional layer of protection against DNS-based DoS attacks.
Systematic Troubleshooting
Resolution and Performance Issues
$ dig +stats example.com
$ dig +trace example.com
$ dig @8.8.8.8 example.com +norecurse
These commands help diagnose DNS resolution issues by showing detailed statistics, tracing the resolution path, and testing specific nameservers.
Propagation Verification
$ for ns in $(dig +short NS example.com); do
echo "Checking $ns:"
dig @$ns example.com A +short
done
This script checks all authoritative nameservers for a domain to verify consistent record data, helping identify propagation issues.
$ watch -n 60 "dig example.com +nocmd +noall +answer"This command monitors TTL countdown in real-time, helping you track propagation progress after making DNS changes.
DNSSEC Validation Issues
$ dig +dnssec +cd example.com
$ for resolver in 1.1.1.1 8.8.8.8 9.9.9.9; do
echo "Testing $resolver:"
dig @$resolver example.com +dnssec +multiline
done
These commands help debug DNSSEC validation issues by bypassing validation checks and testing against different public resolvers.
Reverse DNS Verification
#!/bin/bash
# Check FCrDNS
ip=$(dig example.com A +short)
reverse=$(dig -x $ip +short)
forward=$(dig ${reverse%.} A +short)
if [ "$ip" = "$forward" ]; then
echo "FCrDNS passed"
else
echo "FCrDNS failed"
fi
This script verifies forward-confirmed reverse DNS, which is important for email deliverability and security.
Modern DNS Inspection Tools
DNSdist - DNS Load Balancer with Analytics
$ apt-get install dnsdist
$ cat << EOF > /etc/dnsdist/dnsdist.conf
setLocal("0.0.0.0:53")
addACL("0.0.0.0/0")
setWebserverConfig("0.0.0.0:8083", "admin", "password")
EOF
$ systemctl restart dnsdist
This installs and configures DNSdist, a powerful DNS load balancer that provides detailed analytics and filtering capabilities.
DNStap - DNS Traffic Capture
# Add to /etc/named.conf
options {
dnstap { client; auth; resolver; forwarder; };
dnstap-output file "/var/log/named/dnstap.log";
};
$ apt-get install dnstap-utils
$ dnstap-read /var/log/named/dnstap.log
This configures BIND to use DNStap for detailed traffic capture and installs utilities to analyze the captured data.
DNSViz - DNSSEC Visualization
$ pip install dnsviz==0.9.3
$ dnsviz probe -d example.com > example.com.json
$ dnsviz graph -T png -o example.com.png example.com.json
This installs DNSViz (using a version compatible with most current Python installations) and generates a visual analysis of a domain's DNSSEC configuration.
ELK Stack for DNS Analytics
filter {
if [type] == "bind_query" {
grok {
match => { "message" => "%{SYSLOGTIMESTAMP:timestamp} queries: info: client %{IP:client_ip}#%{NUMBER:client_port} \(%{HOSTNAME:query}\): query: %{HOSTNAME:query} IN %{WORD:query_type} \+%{WORD:flags} \(%{IP:server_ip}\)" }
}
}
}
This Logstash filter parses BIND query logs for analysis in Elasticsearch and visualization in Kibana, enabling advanced DNS analytics.
DNS Query Inspection Tools via Homebrew for System Administrators
I use or work across both Pop!_OS and macOS environments as part of my DevOps responsibilities. Including DNS query inspection tools installable via Homebrew in this documentation promotes cross-platform consistency and streamlines workflows across diverse development setups. This ensures that system administrators operating in multi-platform environments can adopt a uniform approach to tooling and diagnostics, regardless of their underlying OS.
It goes wthout saying that it is essential to review each tool’s repository; not only to become familiar with its capabilities, but also to verify that it is actively maintained. Additionally, avoid redundancy in tooling. In my experience, deep proficiency with a single, reliable tool yields far better results than switching between multiple options without fully understanding their nuances.
Installing Homebrew
If you haven't already installed Homebrew, the missing package manager for macOS (or Linux), run the following command:
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"
1. dig (Domain Information Groper)
The most versatile DNS query tool, providing detailed information about DNS records. "dig" commands works on macOS without the need for additional installation. But if you must, then:
$ brew install bind
$ dig example.com
$ dig example.com A +short
$ dig example.com MX
$ dig @8.8.8.8 example.com NS
$ dig +trace example.com
The +trace option is particularly useful for troubleshooting as it shows the complete DNS resolution path from root servers.
2. dnstracer
Traces DNS queries through the DNS server hierarchy, showing which nameservers are queried.
$ brew install dnstracer
$ dnstracer example.com
$ dnstracer -v -o example.com
3. dnsmap
Discovers subdomains through brute-force methods, helpful for security auditing.
$ brew install dnsmap
$ dnsmap example.com
$ dnsmap example.com -w /path/to/wordlist.txt -r /path/to/results.txt
4. mtr (My Traceroute)
Combines ping and traceroute functionalities to help diagnose routing and DNS issues.
$ brew install mtr
$ sudo mtr example.com
$ sudo mtr --report example.com
5. dnsperf
DNS server performance testing tool that measures query response times and throughput.
$ brew install dnsperf
$ dnsperf -s 8.8.8.8 -d queryfile.txt -c 10 -l 30
You'll need to create a query file with domain names, one per line.
6. dnstop
A tool that displays DNS traffic statistics, useful for monitoring DNS server activity.
$ brew install dnstop
$ sudo dnstop eth0
$ sudo dnstop -l 10 eth0
7. q (dns-query tool)
A lightweight command-line DNS client with a simplified syntax.
$ brew tap natesales/repo https://github.com/natesales/repo
$ q example.com
$ q example.com mx
$ q example.com @8.8.8.8
8. massdns
A high-performance DNS stub resolver for bulk lookups and reconnaissance.
$ brew install massdns
$ massdns -r resolvers.txt -t A -w results.txt domains.txt
$ massdns -r resolvers.txt -t A -o S -w results.txt domains.txt
9. doggo
A modern command-line DNS client with colorful output and intuitive options.
$ brew install doggo
$ doggo example.com
$ doggo example.com MX
$ doggo example.com @8.8.8.8
$ doggo example.com --json
10. kdig (Knot DNS dig)
An alternative to dig with some extended features from the Knot DNS project.
$ brew install knot
$ kdig example.com
$ kdig +dnssec example.com
$ kdig +tls @1.1.1.1 example.com
Creating a DNS Health Check Script
#!/bin/bash
# DNS Health Check Script
DOMAIN=$1
NS_SERVERS=$(dig NS $DOMAIN +short)
echo "Running DNS health check for $DOMAIN"
echo "----------------------------------------"
# Check NS records consistency
echo "Checking NS records consistency..."
for NS in $NS_SERVERS; do
NS_IP=$(dig A $NS +short)
echo " $NS ($NS_IP)"
# Compare NS records from each nameserver
NS_FROM_SERVER=$(dig @$NS NS $DOMAIN +short)
DIFF=$(diff <(echo "$NS_SERVERS" | sort) <(echo "$NS_FROM_SERVER" | sort))
if [ -n "$DIFF" ]; then
echo " WARNING: NS records from $NS don't match:"
echo "$DIFF"
fi
done
# Check A records consistency
echo "Checking A records consistency..."
for NS in $NS_SERVERS; do
A_RECORD=$(dig @$NS A $DOMAIN +short)
echo " $NS: $A_RECORD"
done
# Check SOA records
echo "Checking SOA records..."
for NS in $NS_SERVERS; do
SOA=$(dig @$NS SOA $DOMAIN +short)
echo " $NS: $SOA"
done
# Check DNSSEC
echo "Checking DNSSEC..."
DNSSEC=$(dig $DOMAIN +dnssec +short)
if [ -n "$DNSSEC" ]; then
echo " DNSSEC is enabled"
# Check DNSKEY
DNSKEY=$(dig $DOMAIN DNSKEY +short)
echo " DNSKEY records: $(echo "$DNSKEY" | wc -l | tr -d ' ')"
else
echo " DNSSEC is not enabled"
fi
echo "----------------------------------------"
echo "DNS health check complete"
$ chmod +x dns_health_check-linux.sh
$ ./dns_health_check-linux.sh example.com
Worth mentioning that you should adapt the DNS Health Check script to work reliably on macOS (zsh) by replacing process substitution with temporary files:
#!/bin/bash
#!/bin/bash
# DNS Health Check Script (zsh-compatible)
DOMAIN=$1
if [ -z "$DOMAIN" ]; then
echo "Usage: $0 domain.com"
exit 1
fi
NS_SERVERS=$(dig NS "$DOMAIN" +short)
echo "Running DNS health check for $DOMAIN"
echo "----------------------------------------"
# Check NS records consistency
echo "Checking NS records consistency..."
for NS in $NS_SERVERS; do
NS_IP=$(dig A "$NS" +short)
echo " $NS ($NS_IP)"
NS_FROM_SERVER=$(dig @"$NS" NS "$DOMAIN" +short)
TMP1=$(mktemp)
TMP2=$(mktemp)
echo "$NS_SERVERS" | sort > "$TMP1"
echo "$NS_FROM_SERVER" | sort > "$TMP2"
DIFF=$(diff "$TMP1" "$TMP2")
rm -f "$TMP1" "$TMP2"
if [ -n "$DIFF" ]; then
echo " WARNING: NS records from $NS don't match:"
echo "$DIFF"
fi
done
# Check A records consistency
echo "Checking A records consistency..."
for NS in $NS_SERVERS; do
A_RECORD=$(dig @"$NS" A "$DOMAIN" +short)
echo " $NS: $A_RECORD"
done
# Check SOA records
echo "Checking SOA records..."
for NS in $NS_SERVERS; do
SOA=$(dig @"$NS" SOA "$DOMAIN" +short)
echo " $NS: $SOA"
done
# Check DNSSEC
echo "Checking DNSSEC..."
DNSSEC=$(dig "$DOMAIN" +dnssec +short)
if [ -n "$DNSSEC" ]; then
echo " DNSSEC is enabled"
DNSKEY=$(dig "$DOMAIN" DNSKEY +short)
echo " DNSKEY records: $(echo "$DNSKEY" | wc -l | tr -d ' ')"
else
echo " DNSSEC is not enabled"
fi
echo "----------------------------------------"
echo "DNS health check complete"
$ chmod +x dns_health_check-macOS.sh
$ ./dns_health_check-macOS.sh example.com
Troubleshooting Common DNS Issues
DNS Propagation Delay
To check if DNS changes have propagated globally:
$ dig +trace example.com
$ dig @8.8.8.8 example.com # Check Google DNS
$ dig @1.1.1.1 example.com # Check Cloudflare DNS
$ dig @208.67.222.222 example.com # Check OpenDNS
DNS Caching Issues
To check and clear DNS cache on different systems:
# macOS
$ sudo dscacheutil -flushcache; sudo killall -HUP mDNSResponder
# Linux (systemd)
$ sudo systemd-resolve --flush-caches
# Linux (nscd)
$ sudo service nscd restartDNSSEC Validation Issues
To debug DNSSEC validation issues:
$ dig +dnssec example.com
$ dig +multi +dnssec DNSKEY example.com
$ dig +multi +dnssec DS example.com
This collection of Homebrew-installable DNS tools provides system administrators with powerful capabilities for troubleshooting, monitoring, and securing DNS infrastructure. For complex environments, consider developing custom scripts that combine these tools to automate routine DNS health checks and monitoring.
For cPanel and Plesk environments, these tools can complement the built-in DNS management interfaces and help diagnose issues that may not be apparent through the control panel.
Common Pitfalls to Avoid
- Forgetting TTL implications: Changes won't propagate instantly; always consider TTL values (the lower, the better) when planning updates.
- Ignoring DNSSEC key rotation: Regularly rotate DNSSEC keys and monitor expiration dates to prevent validation failures.
- Overlooking recursive resolver configuration: Misconfigured resolvers can cause resolution delays or failures.
- Neglecting zone file syntax: A single syntax error can invalidate an entire zone file.
- Insufficient logging: Enable comprehensive logging before problems occur to aid troubleshooting.
- Forgetting to check parent zone delegation: Issues at the parent zone can affect your domain's resolution.
Remember that DNS is not just a critical service but also a security boundary, making regular inspection and monitoring essential components of your operational procedures.
By Trax Armstrong, WebHostingM Cloud Infrastructure Team




























