What is DNS?
The Domain Name System (DNS) is a foundational technology that translates domain names (like example_domain.com) into IP addresses, enabling browsers and other applications to locate network resources. It also enables us to use easy-to-remember domain names instead of numerical IP addresses to access services on networks such as the internet.
DNS resolution is a prerequisite for most communications, including HTTPS and SMTP, which rely on IP addresses to connect devices across the internet.
Before secure communications like HTTPS or email (SMTP) can begin, DNS translates (or "resolves") the requested domain name into the actual address a computer understands and routes to – a step known as "resolution".
This process typically starts with a DNS stub resolver on endpoint devices, supporting client applications by translating human-readable names into network addresses.
These queries proceed through a chain of DNS servers, configured as per-hop, meaning every DNS server-to-server connection depends on their setup and topology.
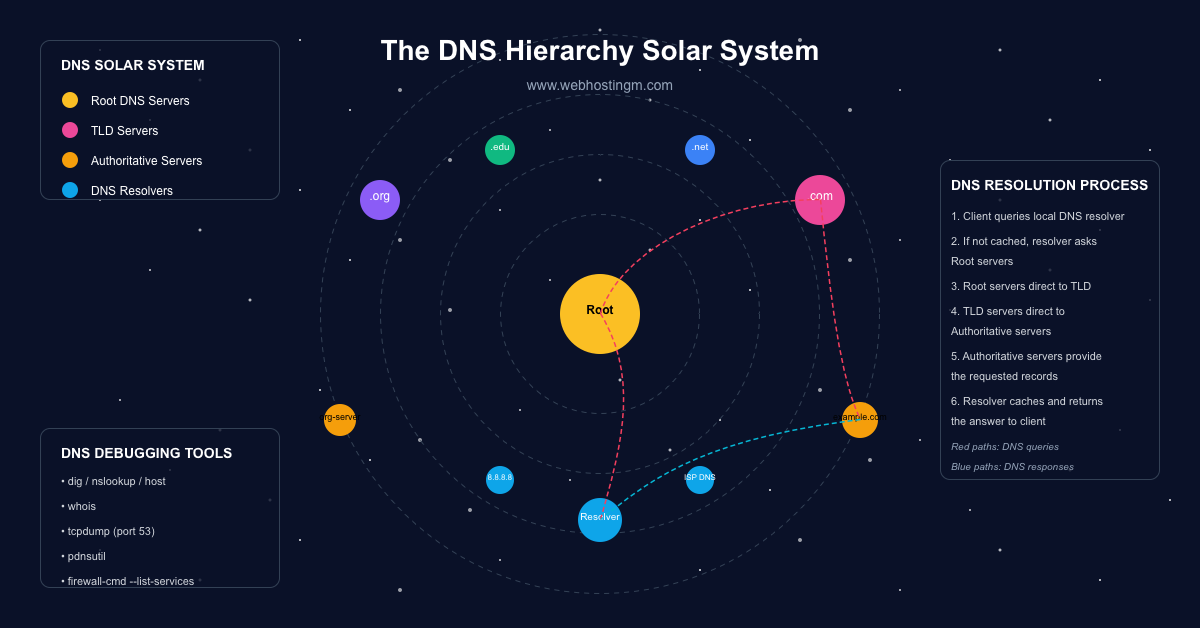
Types of DNS Servers and Roles
- Stub Resolver: Runs on client devices, forwarding queries to a DNS resolver.
- Recursive Resolver: Receives queries from stub resolvers, "walks" the DNS hierarchy to find answers.
- Authoritative Server: Holds DNS records for domains; provides final answers in the resolution process.
- Forwarders: DNS servers configured to forward queries to other DNS servers.
Components such as NS (nameserver) and glue records maintain the chain of delegation within DNS zones.
Modern Extensions and DNS Security
DNSSEC: Securing DNS Integrity
DNS Security Extensions (DNSSEC) add layers of authentication and data integrity, guaranteeing that DNS data was not tampered with in transit. DNSSEC consists of two complementary roles:
- Validation (Recursive): Validates signatures on DNS data and ensures answers haven't been forged.
- Signing (Authoritative): Publishes signed answers/data.
Key setup and requirements:
- Keys are generated and stored on authoritative servers – no third-party certificates are needed.
- All components in the DNS chain (resolvers, authoritative servers, registrars) must support DNSSEC for secure validation.
- Audit and coordination with domain registrars is critical.
DNSSEC provides authenticity and integrity, but does not offer confidentiality or domain filtering.
Pre-Requirements for DNS Troubleshooting on Linux
- Linux server or workstation with administrative privileges
- Access to relevant DNS server or service (local or remote)
- Network connectivity to test DNS resolution
Common DNS Troubleshooting Steps
- Check Local Network Configuration
Ensure your system has an IP address and the correct DNS server configuration:Show IP address (Linux)$ ip aCheck DNS configuration$ cat /etc/resolv.conf - Test Basic Name Resolution
Usedigornslookupto verify DNS queries:A successful response indicates functional DNS resolution. If failures occur, verify the DNS server addresses and network routing.$ dig example.com $ nslookup example.com - Check for Firewall Blocking
Outbound port 53 (TCP/UDP) should be allowed from your machine to approved DNS servers. To inspect Firewalld settings:$ sudo firewall-cmd --list-services $ sudo firewall-cmd --list-portsA common best practice is to block any TCP/UDP port 53 outbound traffic from anything except DNS servers your organization controls. If you are allowing clients on the enterprise network to connect to any external DNS recursive resolvers, with or without encrypted DNS, you could fall victim to another DNSChanger-style attack..Allow DNS through Firewalld$ sudo firewall-cmd --permanent --add-service=dns $ sudo firewall-cmd --reload - Inspect DNS Records and Zone Files
In case of persistent failures, verify that DNS has the correct NS (nameserver), glue, A, MX, and CNAME records, and no "dangling" or abandoned records exist, as these can cause hijacking or misrouting. Regular audits ensure DNS data matches the intended architecture. - Monitoring & Anomaly Detection
Monitor DNS queries and responses to detect anomalies such as:- High query volumes for the same or suspicious domains ("rapid fire" pattern)
- Consistent DNS response sizes (may indicate malware exfiltration)
- Frequent NXDOMAIN (nonexistent domain) responses—possible indication of malware or misconfiguration
- Audit DNS Server Security
- Regularly update server software (bind, unbound, etc.) - Restrict recursion to trusted clients only - Use secure credentials for DNS hosts and registrars - Monitor for account breaches or unauthorized record changes - Leverage Encrypted DNS Carefully
For organizations, consider deploying internal encrypted DNS (DoT/DoH) and avoid using only public encrypted DNS servers. Balance privacy and security controls by collaborating across your DNS and security teams. - Automate DNS Management
Integrating DNS provisioning/deprovisioning with infrastructure automation reduces dangling records and improves overall security.
DNS in DevOps: Docker, Ansible, Terraform, and Vagrant
Docker
DNS resolution or configuration issues inside Docker containers often stem from default DNS settings or network restrictions. To explicitly set a DNS server for a container:
$ docker run --dns 8.8.8.8 -it ubuntu bash
To inspect a running container's DNS settings:
$ docker exec <container_name> cat /etc/resolv.conf
Always ensure the container has network connectivity. Check using:
$ ping -c 3 google.com
Ansible
To automatically enforce DNS configuration on target Linux hosts, use the lineinfile or template modules to specify DNS servers in /etc/resolv.conf (or appropriate config file for your OS). You can also use modules to install and configure BIND (named) or other DNS software, validating the configuration using playbooks.
- name: Ensure DNS resolver is configured
lineinfile:
dest: /etc/resolv.conf
regexp: '^nameserver'
line: 'nameserver 8.8.8.8'
state: present
backup: yes
Terraform
Terraform provides robust DNS management capabilities through various provider plugins (AWS, GCP, Azure, etc.). You can create, update, and manage DNS records as part of your infrastructure deployment.
resource "aws_route53_zone" "primary" {
name = "example.com"
}
resource "aws_route53_record" "www" {
zone_id = aws_route53_zone.primary.zone_id
name = "www.example.com"
type = "A"
ttl = "300"
records = ["192.168.1.1"]
}
resource "google_dns_managed_zone" "example_zone" {
name = "example-zone"
dns_name = "example.com."
description = "Example DNS zone"
}
resource "google_dns_record_set" "a" {
name = "www.example.com."
managed_zone = google_dns_managed_zone.example_zone.name
type = "A"
ttl = 300
rrdatas = ["192.168.1.1"]
}
For custom DNS solutions, you can use the terraform-provider-dns to manage records on various DNS servers:
provider "dns" {
update {
server = "192.168.1.1"
}
}
resource "dns_a_record_set" "www" {
zone = "example.com."
name = "www"
addresses = [
"192.168.1.1",
"192.168.1.2",
]
ttl = 300
}
Vagrant
Add or adjust DNS settings in your Vagrantfile by using config.vm.provider "virtualbox" and config.vm.network options, or by provisioning a script to modify /etc/resolv.conf.
Vagrant.configure("2") do |config|
config.vm.provision "shell", inline: <<-SHELL
echo "nameserver 8.8.8.8" | sudo tee /etc/resolv.conf
SHELL
end
DNS Troubleshooting Gotchas and Security Best Practices
- Never use default or public DNS servers in enterprise environments unless assessed and approved.
- Block all outbound DNS except to your organization’s resolvers when possible.
- Apply strong password and multifactor authentication for DNS hosting and registrar accounts.
- Regularly audit DNS records, including NS, MX, CNAME, and verify against your intended service inventory.
- Implement SIEM monitoring and alerting based on anomalous DNS activity for early threat detection.
Linux Tools & Packages for DNS
- Install DNS Utilities:
$ sudo apt-get install dnsutils # Debian/Ubuntu $ sudo yum install bind-utils # RHEL/CentOS/Fedora - PowerDNS Management with pdnsutil:
# Install PowerDNS and utilities $ sudo apt install pdns-server pdns-backend-mysql # Debian/Ubuntu $ sudo yum install pdns pdns-backend-mysql # RHEL/CentOSCommon pdnsutil operations:
# Create a new zone $ pdnsutil create-zone example.com # Add DNS records $ pdnsutil add-record example.com www A 192.168.1.10 $ pdnsutil add-record example.com mail MX "10 mail.example.com" # Edit an existing zone $ pdnsutil edit-zone example.com # Increase SOA serial after changes $ pdnsutil increase-serial example.com # List all zones $ pdnsutil list-all-zones # DNSSEC operations $ pdnsutil secure-zone example.com $ pdnsutil show-zone example.com - Firewall Management (if running Firewalld):
$ sudo firewall-cmd --get-services $ sudo firewall-cmd --info-service=dns
Debugging DNS Issues
- Check DNS Configuration:
Inspect
/etc/resolv.confon Linux systems for correct nameserver entries.$ cat /etc/resolv.conf $ systemd-resolve --status # For systemd-based systems - Test Basic DNS Resolution:
$ dig example.com $ nslookup example.com $ host example.com - Trace DNS Resolution Path:
$ dig +trace example.com $ dig @8.8.8.8 example.com # Test using specific DNS server - Check for Network-Level Blocks:
Firewalls or SELinux/AppArmor may block port 53 for DNS. Confirm open ports:
$ sudo firewall-cmd --list-ports $ sudo firewall-cmd --list-services $ sudo netstat -tulpn | grep :53 - Verify DNS Server Operations:
$ systemctl status named # BIND DNS server $ systemctl status pdns # PowerDNS server $ journalctl -u named # Check DNS server logs - DNSSEC Validation and Testing:
For DNSSEC-enabled domains, use these commands to check status and records:
$ dig +dnssec example.com # Look for "ad" flag in response $ whois domain.tld | egrep -i "DNSSEC|signed" # Check DNSSEC registration status $ dig ds domain.tld +short # Check DS records $ dig domain.tld DNSKEY @10.2.34.14 +short # Check DNSKEY records $ delv domain.tld # DNSSEC validation debugging - DNSSEC Management:
Important operations for DNSSEC configuration:
# PowerDNS DNSSEC operations $ pdnsutil secure-zone example.com # Enable DNSSEC for a zone $ pdnsutil show-zone example.com # Check DNSSEC status # Google Cloud DNS DNSSEC management $ gcloud dns managed-zones update EXAMPLE_ZONE --dnssec-state off # Disable DNSSEC # IMPORTANT: Before disabling DNSSEC, always remove DS records at your registrar first # and wait for cache expiration to prevent resolution failures - Monitor DNS Queries for Anomalies:
$ sudo tcpdump -i any port 53 # Capture all DNS traffic $ sudo tcpdump -i any -s0 port 53 -w dns_capture.pcap # Save to file for analysis $ sudo dnstop eth0 # Real-time DNS traffic monitoring - DNS Record Auditing and Validation:
$ dig ANY example.com # Get all records (may be filtered by some servers) $ dig -t TXT example.com # Check TXT records (SPF, DKIM, etc.) $ dig -t MX example.com # Check mail exchanger records $ host -t NS example.com # Check nameserver records - Check DNS Propagation:
Verify if DNS changes have propagated globally:
$ dig example.com @ns1.example.com $ dig example.com @8.8.8.8 $ dig example.com @1.1.1.1Or use online tools like whatsmydns.net to check propagation across multiple locations.
- Performance Testing:
$ dig +stats example.com # Show query statistics $ time dig example.com # Measure resolution time $ dig +tries=1 +timeout=1 example.com # Test with strict timeout - DNS Security Auditing:
$ dig +short txt _dmarc.example.com # Check DMARC record $ dig +short txt example.com # Check SPF record $ dig +short caa example.com # Check CAA records
Up-to-Date Apache on Linux
- Install Apache 2.4+ (RHEL/CentOS/Fedora):
$ sudo yum install httpd - On Debian/Ubuntu systems:
$ sudo apt-get install apache2
Python and pip for Automation
Use pip3 with Python 3.6+ (or the version currently supported by your distribution/upstream). For automation and configuration (e.g., Ansible):
$ sudo apt-get install python3-pip # Debian/Ubuntu
$ sudo yum install python3-pip # RHEL/CentOS/FedoraEnsure pip (or pip3) and python-devel/python3-devel are installed before managing DNS automation frameworks.
Pro Tips & Gotchas
- Do not DNSSEC-sign dynamic or internal zones, as frequent updates make zone re-signing complex
- Some DNS features (e.g., server load balancing or apex record flattening) may complicate or prevent DNSSEC signing.
- DNSSEC does not prevent attackers from registering malicious domains and signing them.
- Monitor and regularly audit both DNS records and account controls—DNS is a favorite target for attackers.
- Prioritize proper credential management for all DNS-related accounts.
Summary Table: DNS Server Types
| Type | Role | Key Functions |
|---|---|---|
| Stub Resolver | Client-side | Initial query, forwards to resolver |
| Recursive Resolver | Mid-tier | Finds answer for client, validates DNSSEC |
| Authoritative Server | Final answer | Hosts records, signs data (DNSSEC) |
Further Security Considerations
DNS is central to your network security posture. Secure both servers and endpoints, audit regularly for record abandonment or suspicious patterns, and ensure automation removes DNS entries when assets are decommissioned. Keep up-to-date on DNS standards and evolving privacy offerings, and use DNS data as a valuable resource for threat detection and incident response initiatives.
Subscribe to our newsletter for further details and deeper strategies in DNS security, automation, deep DNS query inspection, and auditing.
Written by Trax Armstrong, a Cloud Infrastructure Engineer | cPanel & WHM System Admin | Plesk System Admin | Linux SysAdmin specializing in Google Cloud Platform (GCP), AWS, OCI, and hybrid cloud solutions.




























